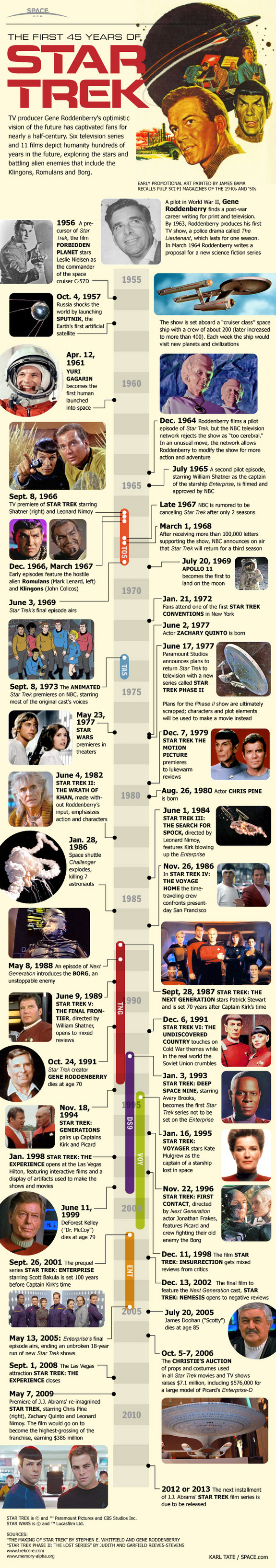
This part covers the following config.xml components for Windows XP:
--------------------------------------------------------------------------------------------------
<component displayname="Microsoft-Windows-Microsoft-Data-Access-Components-(MDAC)-ODBC-DriverManager-Dll-DL" migrate="yes" ID="http://www.microsoft.com/migration/1.0/migxmlext/cmi/microsoft-windows-microsoft-data-access-components-(mdac)-odbc-drivermanager-dll-dl/microsoft-windows-microsoft-data-access-components-(mdac)-odbc-drivermanager-dll-dl/settings"/>
<component displayname="Microsoft-Windows-COM-ComPlus-Setup-DL" migrate="yes" ID="http://www.microsoft.com/migration/1.0/migxmlext/cmi/microsoft-windows-com-complus-setup-dl/microsoft-windows-com-complus-setup-dl/settings"/>
<component displayname="Microsoft-Windows-COM-Base-DL" migrate="yes" ID="http://www.microsoft.com/migration/1.0/migxmlext/cmi/microsoft-windows-com-base-dl/microsoft-windows-com-base-dl/settings"/>
<component displayname="Microsoft-Windows-ICM-Profiles-DL" migrate="yes" ID="http://www.microsoft.com/migration/1.0/migxmlext/cmi/microsoft-windows-icm-profiles-dl/microsoft-windows-icm-profiles-dl/settings"/>
<component displayname="Microsoft-Windows-feclient-DL" migrate="yes" ID="http://www.microsoft.com/migration/1.0/migxmlext/cmi/microsoft-windows-feclient-dl/microsoft-windows-feclient-dl/settings"/>
<component displayname="Microsoft-Windows-dpapi-keys-DL" migrate="yes" ID="http://www.microsoft.com/migration/1.0/migxmlext/cmi/microsoft-windows-dpapi-keys-dl/microsoft-windows-dpapi-keys-dl/settings"/>
<component displayname="Microsoft-Windows-Crypto-keys-DL" migrate="yes" ID="http://www.microsoft.com/migration/1.0/migxmlext/cmi/microsoft-windows-crypto-keys-dl/microsoft-windows-crypto-keys-dl/settings"/>
<component displayname="Microsoft-Windows-CAPI2-certs-DL" migrate="yes" ID="http://www.microsoft.com/migration/1.0/migxmlext/cmi/microsoft-windows-capi2-certs-dl/microsoft-windows-capi2-certs-dl/settings"/>
</component>
</component>
<component displayname="Accessibility" migrate="yes" ID="accessibility">
<component displayname="Accessibility Settings" migrate="yes" ID="accessibility\accessibility_settings">
<component displayname="Microsoft-Windows-accessibilitycpl-DL" migrate="yes" ID="http://www.microsoft.com/migration/1.0/migxmlext/cmi/microsoft-windows-accessibilitycpl-dl/microsoft-windows-accessibilitycpl-dl/settings"/>
</component>
</component>
--------------------------------------------------------------------------------------------------
ODBC & MDAC
Config Entry
<component displayname="Microsoft-Windows-Microsoft-Data-Access-Components-(MDAC)-ODBC-DriverManager-Dll-DL" migrate="yes" ID="http://www.microsoft.com/migration/1.0/migxmlext/cmi/microsoft-windows-microsoft-data-access-components-(mdac)-odbc-drivermanager-dll-dl/microsoft-windows-microsoft-data-access-components-(mdac)-odbc-drivermanager-dll-dl/settings"/>
Config Manifest
"\USMT\x86\DlManifests\odbc32dll-dl.man"
Behavior Synopsis
Migrates per-user and per-computer ODBC settings from registry and file system.
COM+ Applications
Config Entry
<component displayname="Microsoft-Windows-COM-ComPlus-Setup-DL" migrate="yes" ID="http://www.microsoft.com/migration/1.0/migxmlext/cmi/microsoft-windows-com-complus-setup-dl/microsoft-windows-com-complus-setup-dl/settings"/>
Config Manifest
"\USMT\x86\DlManifests\microsoft.windows.com.complus.setup.dl.man"
Plugin: Microsoft-Windows-COM-ComPlus-Setup-DL\commig.dl
Behavior Synopsis
Migrates COM+ application settings per-user and per-system. No UI, these are configured by applications.
Critical note: You should always set to NO in the config.xml, when migrating from x86 to x64 computers due to bug, as per KB2481190.
DCOM
Config Entry
<component displayname="Microsoft-Windows-COM-Base-DL" migrate="yes" ID="http://www.microsoft.com/migration/1.0/migxmlext/cmi/microsoft-windows-com-base-dl/microsoft-windows-com-base-dl/settings"/>
Config Manifest
"\USMT\x86\DlManifests\microsoft.windows.com.base-dl.man"
Behavior Synopsis
Migrates OLE (i.e. DCOM) settings and files for the computer.
Image Color Management
Config Entry
<component displayname="Microsoft-Windows-ICM-Profiles-DL" migrate="yes" ID="http://www.microsoft.com/migration/1.0/migxmlext/cmi/microsoft-windows-icm-profiles-dl/microsoft-windows-icm-profiles-dl/settings"/>
Config Manifest
"\USMT\x86\DlManifests\microsoft-windows-icm-profiles-dl.man"
Behavior Synopsis
Migrates printer system color profiles for the computer, which can be modified by users through the add-on Microsoft Color Control Panel Applet.
EFS
Config Entry
<component displayname="Microsoft-Windows-feclient-DL" migrate="yes" ID="http://www.microsoft.com/migration/1.0/migxmlext/cmi/microsoft-windows-feclient-dl/microsoft-windows-feclient-dl/settings"/>
Config Manifest
"\USMT\x86\DlManifests\feclient-dl.man"
Behavior Synopsis
Migrates per-user and per-computer file encryption (EFS) options. These are mainly customized through the registry of act of encryption, there is limited UI, see http://technet.microsoft.com/en-us/library/cc736602(WS.10).aspx.
DPAPI
Config Entry
<component displayname="Microsoft-Windows-dpapi-keys-DL" migrate="yes" ID="http://www.microsoft.com/migration/1.0/migxmlext/cmi/microsoft-windows-dpapi-keys-dl/microsoft-windows-dpapi-keys-dl/settings"/>
Config Manifest
"\USMT\x86\DlManifests\dpapi_keys-dl.man"
Behavior Synopsis
Migrates the DPAPI encryption keys for users and computers. There is no UI for these settings and data.
Certificate Private Keys
Config Entry
<component displayname="Microsoft-Windows-Crypto-keys-DL" migrate="yes" ID="http://www.microsoft.com/migration/1.0/migxmlext/cmi/microsoft-windows-crypto-keys-dl/microsoft-windows-crypto-keys-dl/settings"/>
Config Manifest
"\USMT\x86\DlManifests\crypto_keys-dl.man"
Behavior Synopsis
Copies the certificate private keys for users (but not computer’s private keys, due to behavior described in http://blogs.technet.com/b/askds/archive/2010/12/03/friday-mail-sack-pew-pew-pew-edition.aspx#usmtcert and http://blogs.technet.com/b/askds/archive/2011/05/06/friday-mail-sack-who-am-i-kidding-more-like-monthly-edition.aspx#usmtcert ).
Certificate Public Keys
Config Entry
<component displayname="Microsoft-Windows-CAPI2-certs-DL" migrate="yes" ID="http://www.microsoft.com/migration/1.0/migxmlext/cmi/microsoft-windows-capi2-certs-dl/microsoft-windows-capi2-certs-dl/settings"/>
Config Manifest
"\USMT\x86\DlManifests\capi2_certs-dl.man"
Behavior Synopsis
Copies the certificates with their public keys for users and computers (irrespective of the private keys, as described in http://blogs.technet.com/b/askds/archive/2010/12/03/friday-mail-sack-pew-pew-pew-edition.aspx#usmtcert ).
Accessibility
Config Entry
<component displayname="Microsoft-Windows-accessibilitycpl-DL" migrate="yes" ID="http://www.microsoft.com/migration/1.0/migxmlext/cmi/microsoft-windows-accessibilitycpl-dl/microsoft-windows-accessibilitycpl-dl/settings"/>
Config Manifest
"\USMT\x86\DlManifests\accessibilitycpl-dl.man"
Behavior Synopsis
Copies per-user Accessibility settings like color, narrator, and magnifier, plus mouse and desktop windows settings (some of which are duplicated by the Win32 manifest).
The Complete List and Downloadable Versions
- Understanding the USMT Config.xml Windows XP Downlevel Manifest Behaviors 1.0.docx (download)
- Understanding the USMT Config.xml Windows Vista Manifest Behaviors 1.0.docx (download)
- Understanding what the USMT 4.0 CONFIG manifests migrate (Part 1: Introduction)
- Understanding what the USMT 4.0 CONFIG manifests migrate (Part 2: XP Section A)
- Understanding what the USMT 4.0 CONFIG manifests migrate (Part 3: XP Section B)
- Understanding what the USMT 4.0 CONFIG manifests migrate (Part 4: XP Section C)
- Understanding what the USMT 4.0 CONFIG manifests migrate (Part 5: XP Section D)
- Understanding what the USMT 4.0 CONFIG manifests migrate (Part 6: XP Section E)
- Understanding what the USMT 4.0 CONFIG manifests migrate (Part 7: XP Section F)
- Understanding what the USMT 4.0 CONFIG manifests migrate (Part 8: XP Section G)
- Understanding what the USMT 4.0 CONFIG manifests migrate (Part 9: XP Section H)
- Understanding what the USMT 4.0 CONFIG manifests migrate (Part 10: Vista Section A)
- Understanding what the USMT 4.0 CONFIG manifests migrate (Part 11: Vista Section B)
- Understanding what the USMT 4.0 CONFIG manifests migrate (Part 12: Vista Section C)
- Understanding what the USMT 4.0 CONFIG manifests migrate (Part 13: Vista Section D)
- Understanding what the USMT 4.0 CONFIG manifests migrate (Part 14: Vista Section E)
- Understanding what the USMT 4.0 CONFIG manifests migrate (Part 15: Vista Section F)
- Understanding what the USMT 4.0 CONFIG manifests migrate (Part 16: Vista Section G)
- Understanding what the USMT 4.0 CONFIG manifests migrate (Part 17: Vista Section H)
- Understanding what the USMT 4.0 CONFIG manifests migrate (Part 18: Vista Section I)
- Understanding what the USMT 4.0 CONFIG manifests migrate (Part 19: Vista Section J)
- Understanding what the USMT 4.0 CONFIG manifests migrate (Part 20: Vista Section K)
Ned “better than counting sheep” Pyle
![image_thumb[14] image_thumb[14]](http://blogs.technet.com/cfs-file.ashx/__key/communityserver-blogs-components-weblogfiles/00-00-00-58-02-metablogapi/4186.image_5F00_thumb14_5F00_thumb_5F00_1118EF4A.png)
![image_thumb[15] image_thumb[15]](http://blogs.technet.com/cfs-file.ashx/__key/communityserver-blogs-components-weblogfiles/00-00-00-58-02-metablogapi/3404.image_5F00_thumb15_5F00_thumb_5F00_5C981D01.png)
![image_thumb[16] image_thumb[16]](http://blogs.technet.com/cfs-file.ashx/__key/communityserver-blogs-components-weblogfiles/00-00-00-58-02-metablogapi/8206.image_5F00_thumb16_5F00_thumb_5F00_4C3CA548.png)
![image_thumb[17] image_thumb[17]](http://blogs.technet.com/cfs-file.ashx/__key/communityserver-blogs-components-weblogfiles/00-00-00-58-02-metablogapi/7142.image_5F00_thumb17_5F00_thumb_5F00_3190092F.png)
![image_thumb[18] image_thumb[18]](http://blogs.technet.com/cfs-file.ashx/__key/communityserver-blogs-components-weblogfiles/00-00-00-58-02-metablogapi/4186.image_5F00_thumb18_5F00_thumb_5F00_5DCC9013.png)
![image_thumb[19] image_thumb[19]](http://blogs.technet.com/cfs-file.ashx/__key/communityserver-blogs-components-weblogfiles/00-00-00-58-02-metablogapi/1768.image_5F00_thumb19_5F00_thumb_5F00_1BE5AAC5.png)
![image_thumb[21] image_thumb[21]](http://blogs.technet.com/cfs-file.ashx/__key/communityserver-blogs-components-weblogfiles/00-00-00-58-02-metablogapi/0285.image_5F00_thumb21_5F00_thumb_5F00_1A34DEF1.png)


































































![clip_image006[5] clip_image006[5]](http://blogs.technet.com/cfs-file.ashx/__key/communityserver-blogs-components-weblogfiles/00-00-00-58-02-metablogapi/0285.clip_5F00_image0065_5F00_thumb_5F00_458D5894.jpg)
![clip_image008[5] clip_image008[5]](http://blogs.technet.com/cfs-file.ashx/__key/communityserver-blogs-components-weblogfiles/00-00-00-58-02-metablogapi/5076.clip_5F00_image0085_5F00_thumb_5F00_6DDC8AE8.jpg)